
Testing and compliance
Testing and compliance are two areas which often skipped during the implementation of a DAM system due to budget or time constraints. Other times, the only extend of it is to run through the most important features as part of customer training to see if they behave as expected. And even if testing and compliance are seen as part of an implementation plan, many solution providers forget that those are actually ongoing and never-ending efforts.
In reality, it is wise to invest in proper testing and assessing compliance before going live, so that issues can be found and fixed before a solution is opened to general use. In some cases, it can even lead to non-approval of a solution at the very last minute which can cost your customer and you a lot of money (and prestige). Ongoing testing and compliance efforts will also ensure that a DAM solution is ready for potential future threats, just as the recent Heartbleed bug has shown.
Testing
Generally, the goal of testing is to validate and verify that a DAM solution meets all requirements, works as expected and satisfies the needs of your customer. This can be achieved in areas such as:- System Integration Testing: Are all components of a DAM system properly talking to each other as well as with integrated, 3rd party components/solutions?
- Security Scans: Are your protocols, passwords, encryption standards, ports and certificates safe enough and adhere to set standards?
- Vulnerability Assessments: Scanning your system in order to create a prioritized list of discovered vulnerabilities and how to remediate them.
- Penetration Tests: Simulate specific attacks in order to find out if intruders can gain access in a way they should not be able to.
- Usability Testing: How do endusers evaluate the usability of your DAM solution and what can be improved?
- User Acceptance Testing: Are all requirements of agreed upon specifications met?
- Performance Testing: Does the solution fulfill certain benchmarks in terms of responsiveness and stability under a particular workload?
Compliance
Being compliant means being able to demonstrate to a client that a DAM solution satisfies all regulations, processes and policies imposed internally or by law. This typically includes areas such as:- Security Standards: How does your data and traffic has to be encrypted? What password length and complexity is required? Does your documentation need to stored “at rest”? How often will the security of your DAM system be audited?
- Government Regulations: This includes regulations such as HIPAA, Section 508 Standards (Accessibility & Readability), Intellectual Property Laws, Privacy Laws and much more.
- Approved Software/Vendors/Technologies: Many customers only allow certain vendors or software when you need to use 3rd party software as part of your DAM implementation. Others require or eventually may require open standards such as SQL.
- Software Updates: Do OS patches need to be applied regularly? Does your DAM system need to be upgraded whenever a new release comes out?
Customer Example
To demonstrate how we implemented an ongoing testing and compliance scheme for one of our customers, please see the following diagram: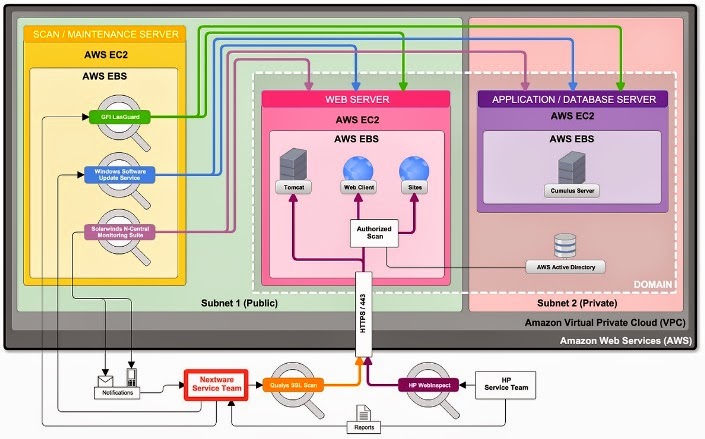
As you can see, we ensure that this particular DAM solution continues to work as expected through a multitude of tools, including:
- HP WebInspect: An automated and configurable web application security and penetration testing tool that mimics real-world hacking techniques and attacks, enabling you to thoroughly analyze your complex web applications and services for security vulnerabilities.
- Qualys SSL Scan: performs a deep analysis of the configuration of your SSL-secured web server and how these settings can be improved.
- Solarwinds N-Central Monitoring Suite: monitors and reports on the up-time of all system components in order to minimize downtime and respond to issues quickly, often before your customer will even notice.
- GFI LanGuard: A vulnerability scanner and patch management software which scans your network’s ports for vulnerabilities and offers remedies.
- Windows Software Update Service (WSUS): Automatically ensures that all critical and non-critical OS patches are applied as they are released.






.png)

